Archives: Projects
Projects

Microsoft Active Directory
MICROSOFT ACTIVE DIRECTORY LAB
Active Directory

Project URL: https://github.com/cecirio/microsoft-active-directory
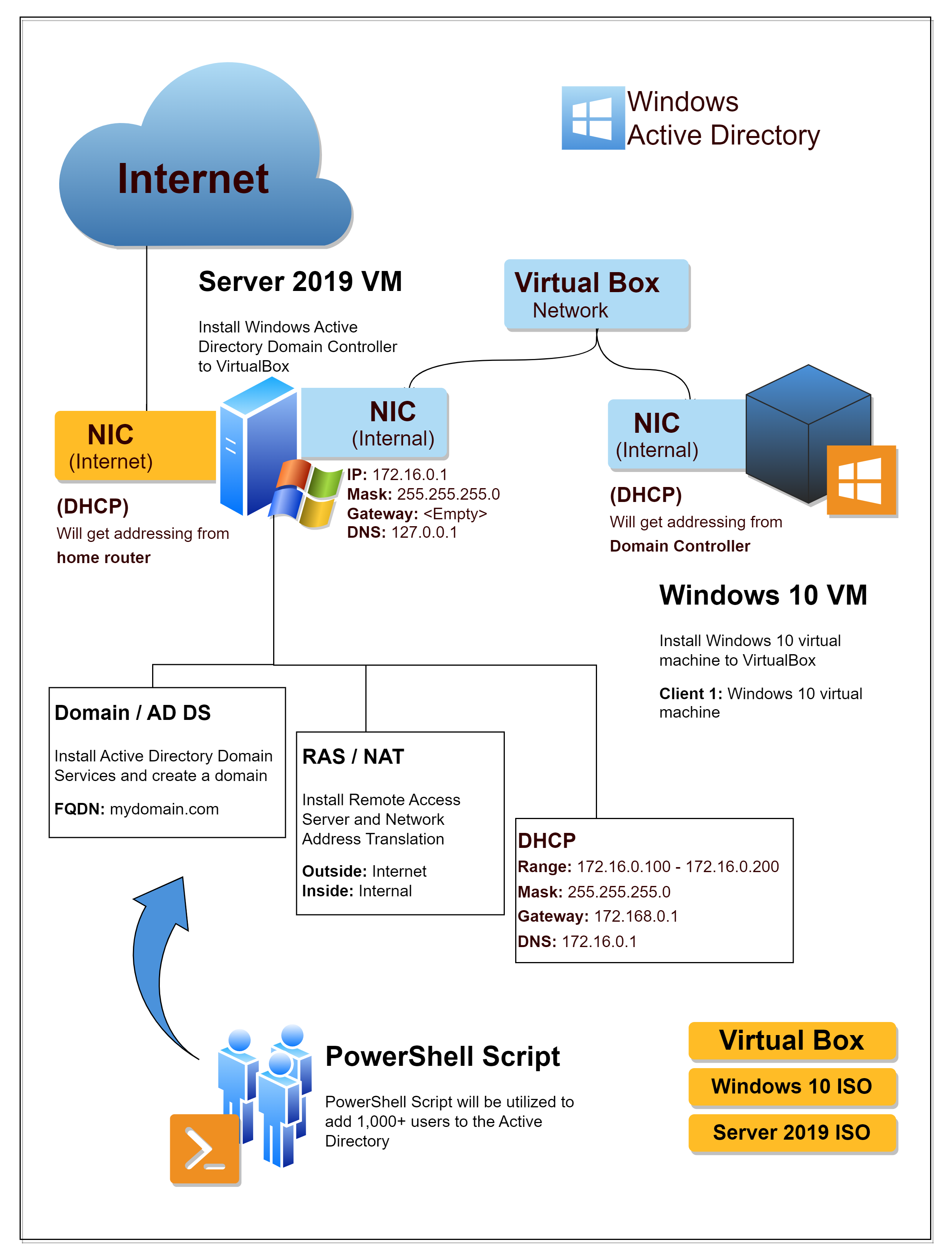
- Installed and configured Windows Server 2019 and Active Directory Domain Services
- Installed and configured a Windows 10 client machine to add to the domain network
- Automated the provision of user accounts with PowerShell
- Set up Remote Access Server (RAS) features to support NAT/PAT
- Implemented and performed maintenance to Windows DNS and DHCP services
- Performed Active Directory Administration tasks to gain user management experience

Python Code
100 DAYS OF CODE: PYTHON
Coding

Project URL: https://github.com/cecirio/100-days-of-code
I made the commitment to code for at least one hour a day for 100 days to learn Python. These are my beginner projects so far:
- Day 01: Working With Variables in Python to Manage Data
- Day 02: Understanding Data Types and How to Manipulate Strings
- Day 03: Control Flow and Logical Operators
- Day 04: Randomisation and Python Lists
- Day 05: Python Loops
- Day 06: Python Functions & Karel
- Day 07: Hangman
- Day 08: Function Parameters & Caesar Cipher
- Day 09: Dictionaries, Nesting and The Secret Auction
- Day 10: Functions with Outputs

Azure Sentinel SIEM
MICROSOFT AZURE SIEM LAB
SIEM Lab

Project URL: https://github.com/cecirio/azure-sentinel-attack-map
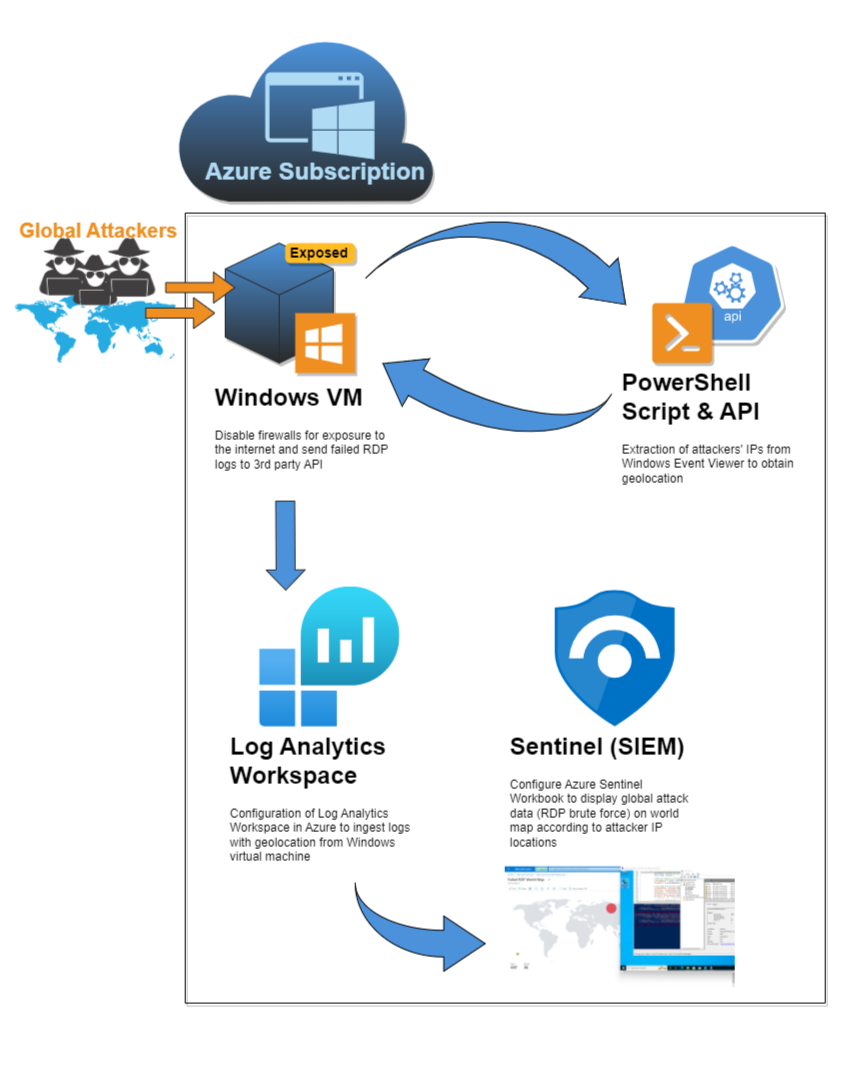
- Used a custom PowerShell script to extract metadata from Windows Event Viewer to have it forwarded to third party API and derive geolocation data
- Configured Log Analytics Workspace in Azure to ingest custom logs containing geographic information (latitude, longitude, state/province, and country)
- Configured Custom Fields in Log Analytics Workspace to map geo data in Azure Sentinel
- Configured Azure Sentinel (Microsoft's cloud SIEM) workbook to display global attack data (RDP brute force) on world map according to physical location and magnitude of attacks

Splunk SIEM
SPLUNK SIEM LAB
SIEM Lab

Company: Flatiron School
- Installed Splunk appliance on a Linux-based Server VM (custom built Ubuntu Server 20.04 in VirtualBox). Configured Splunk to start automatically upon turning on the VM.
- Calculated storage requirements and configured Indexing and upload data sets to ingest data and custom logs for analysis.
- Used Nmap to run a manual scan of my personal network and used Splunk's Asset Discovery App to demonstrate how Asset Management might look inside of a SIEM.
- Designed SIEM Use Cases for specific scenarios and practiced searching using the SPL (Search Processing Language) in order to explain the data and figure out the story behind it. Displayed real incidents attack data in an easily-readable dashboard to generate various reports.
- Configured Splunk alerts and Installed apps such as Windows, *nix, CIM Apps to translate and normalize data from different sources
- Managed regular backups of progress by taking snapshots before critical updates or configurations.